Navigate Cyber Threats
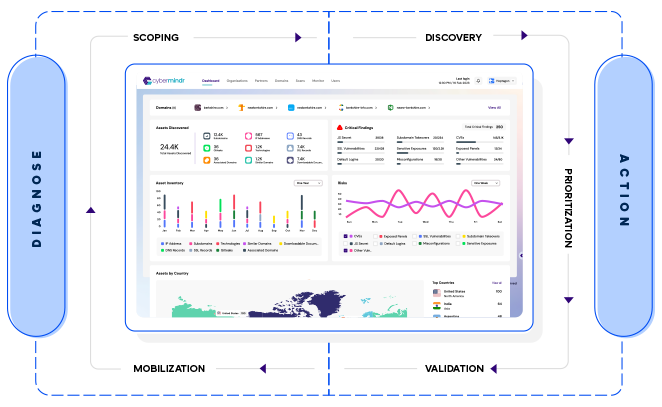
Organizations need to transition strategically from the conventional approach of just identifying vulnerabilities and adhering to cybersecurity frameworks to adopt a risk-centric perspective focused on effectively minimizing real-world exposures. Threat Exposure Discovery streamlines the complex tasks of inventorying, prioritizing and validating rapidly evolving threat exposures in your ever-expanding attack surface.
Cybermindr offers a practical approach to constantly refine priorities. It balances the two important security challenges that every CISO faces: organizations cannot address every issue, yet they also can’t be entirely certain about which vulnerability remediation can be safely deferred.

Why Choose us?
Active identification of systems and network vulnerabilities to reduce security gaps
Develop effective mitigation strategies by prioritizing issues that can be exploited

Meet regulatory requirements, streamline audits and avoid costly fines
“Exposure is more than just the security posture.” – Gartner
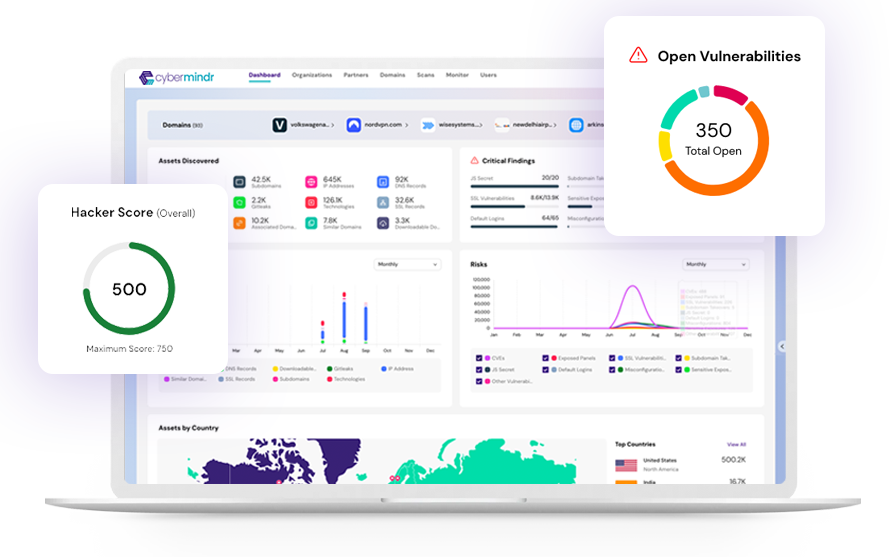
cybermindr platform
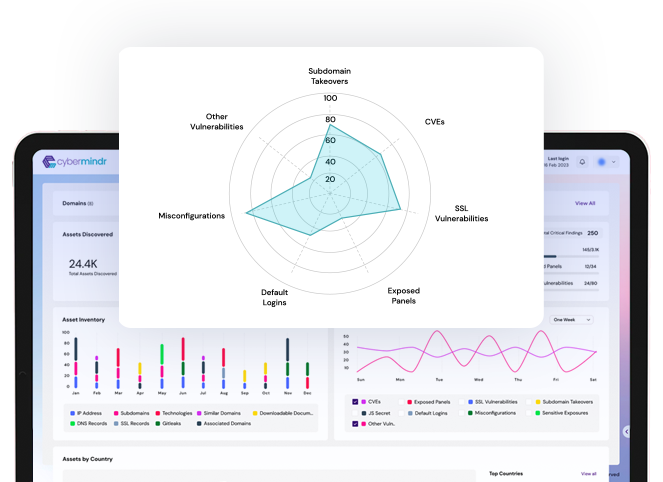
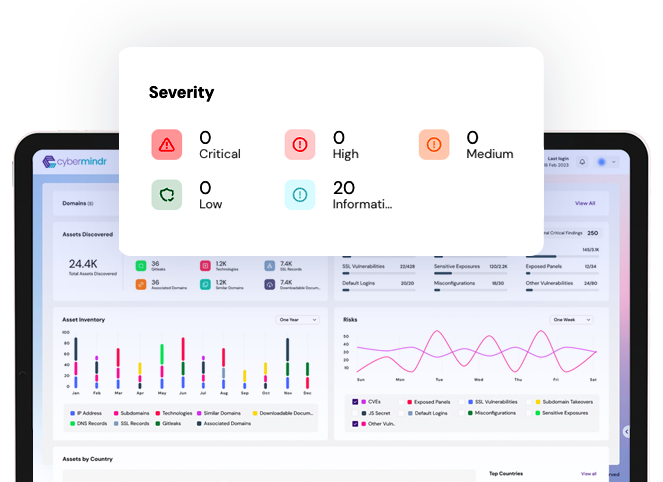
Continuously scan your internet facing assets for known and emerging vulnerabilities
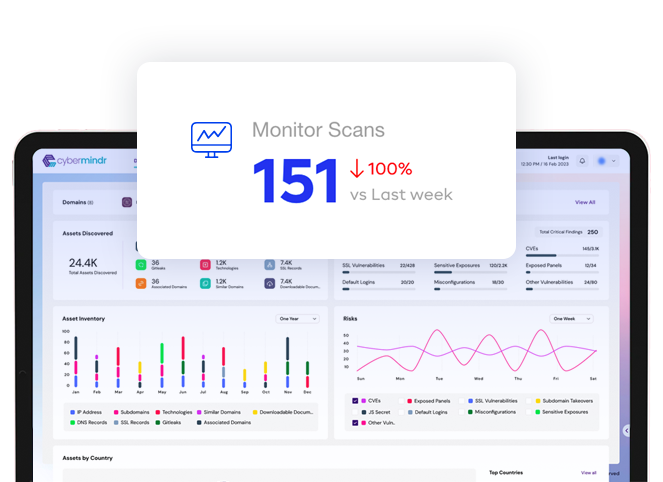
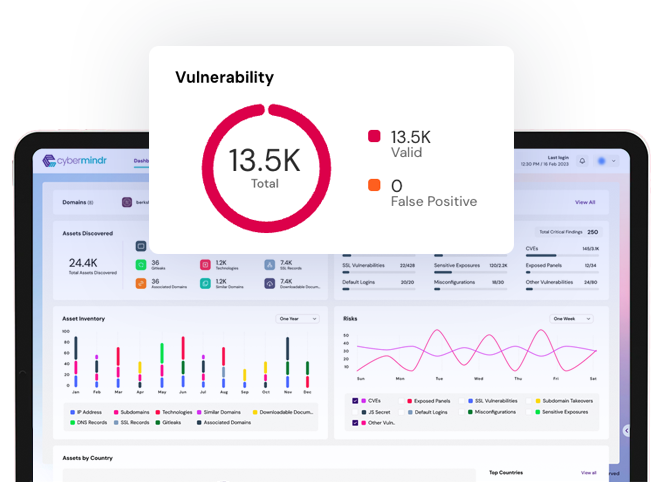
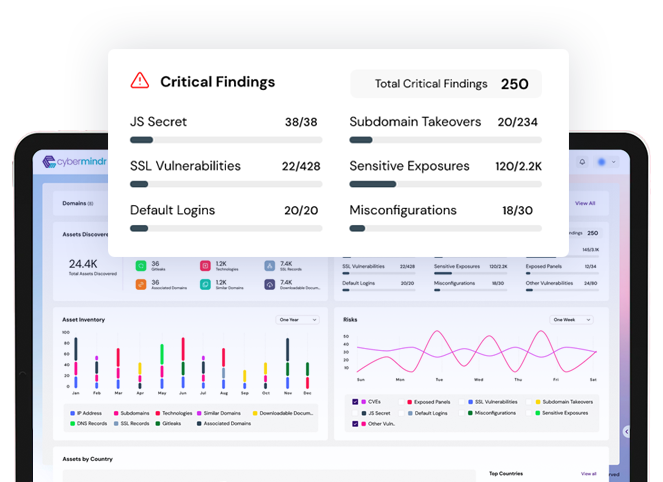
Advanced testing methods looks for vulnerabilities beyond CVEs
Related Use Cases

Gain insights into the cybersecurity posture of your portfolio companies
Read more

Meet regulatory requirements, streamline audits and avoid costly fines.
Read more

Safeguard your assets by minimizing potential risks from third party technologies that your organization uses.
Read more

Conduct in-depth evaluations of potential acquisitions or partnerships.
Read more