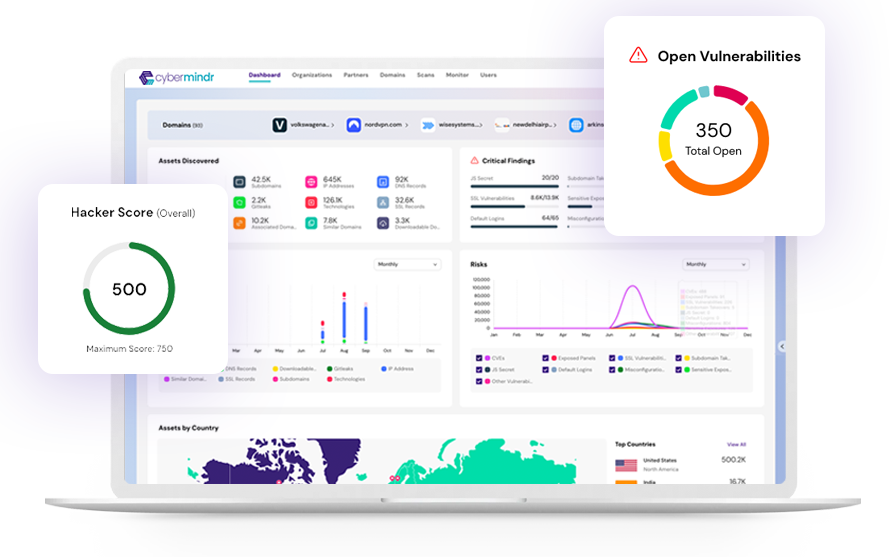
Visibility. Verification. Validation.
While many external assessment tools simply rely on passive data collection methods such as Open-Source Intelligence (OSINT) and broad internet scanners, we take a more comprehensive approach. In addition to ingesting data from many different passive sources, the platform employs a range of active assessment techniques that automatically removes outdated, misattributed & other false positive data.
This reduces dashboard fatigue and offers an accurate and current representation of your cybersecurity posture. The proactive approach helps you to make informed decisions to prioritize vulnerabilities before they are exploited.
Start scan with a domain name
Data from
30+ OSINT sources
Prediction Engine Discover more assets (25%+ additional discovery)
D2 Engine
Deep & Dark Web scans
Validation Engine
vulnerability verification by active methods
Safe exploits with Multi-stage Attack Engine
Reporting Engine
API/ Web/ PDF/ XLS
cybermindr platform
Explore your technology stack comprehensively, from deployed technologies, Domains, Associated Domains, Subdomains, IP Address, DNS Records, SSL Certificates, Technology Stack etc.

Uncover publicly accessible code with potential security risks, exposed API keys, Gitleaks, Javascript keys, backup and hidden files etc.
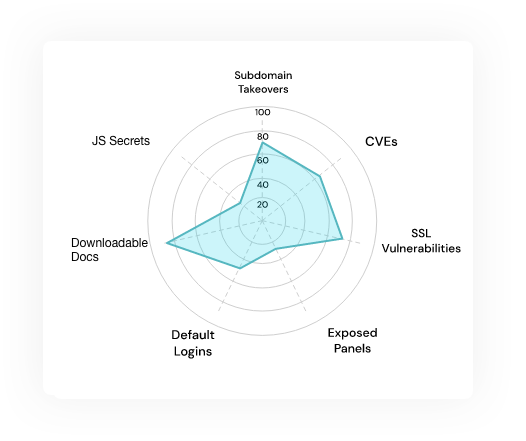
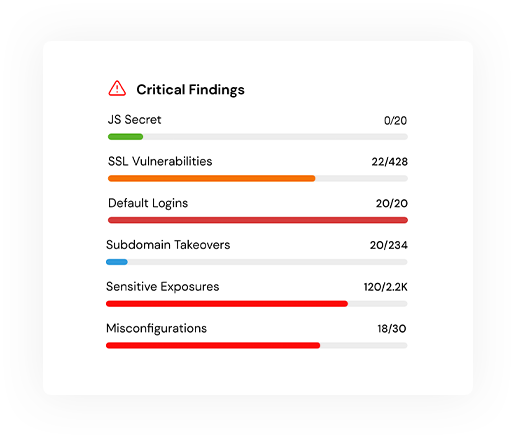
Proactively identify misconfigurations, SSL issues, exposed panels, CVEs (vendor-specific vulnerabilities) and exploitability concerns, Default Credentials, etc.
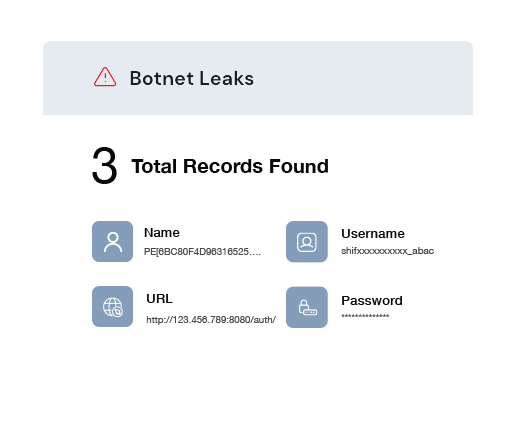
Detect botnet leaks and track leaked credentials currently in circulation on hacker markets & dark web to safeguard your sensitive information.
Traditional ASM tools are built to discover external assets without focusing on issue identification, relying heavily on passive discoveries using open-source data. It doesn’t actively test your security but may reveal mistakes and outdated information present within the system.
CyberMindr Platform actively validates vulnerabilities and executes proof-of-concept exploits during assessments, going beyond traditional Attack Surface Management (ASM) tools. This dynamic approach ensures that identified risks are tangible and actionable.
Know how your organization's security looks to a hacker

Eliminate irrelevant data with precision through active testing

Know the level of threat posed by every vulnerability found

Get real-time actionable data to remediate risks
BENEFITS
Leverage a cloud-based SaaS platform which requires no additional hardware or agent for deployment.
Get access to and run scans for data leaks from across the deep, dark and surface web.
Benefit from a unique validation engine to increase the visibility of easily exploitable attack paths.
Automatically detect, fingerprint and identify exposed digital assets.
Usecases
Take a proactive approach to protecting your data and systems before a cyberattack leads to data breaches, financial losses or reputational damage.