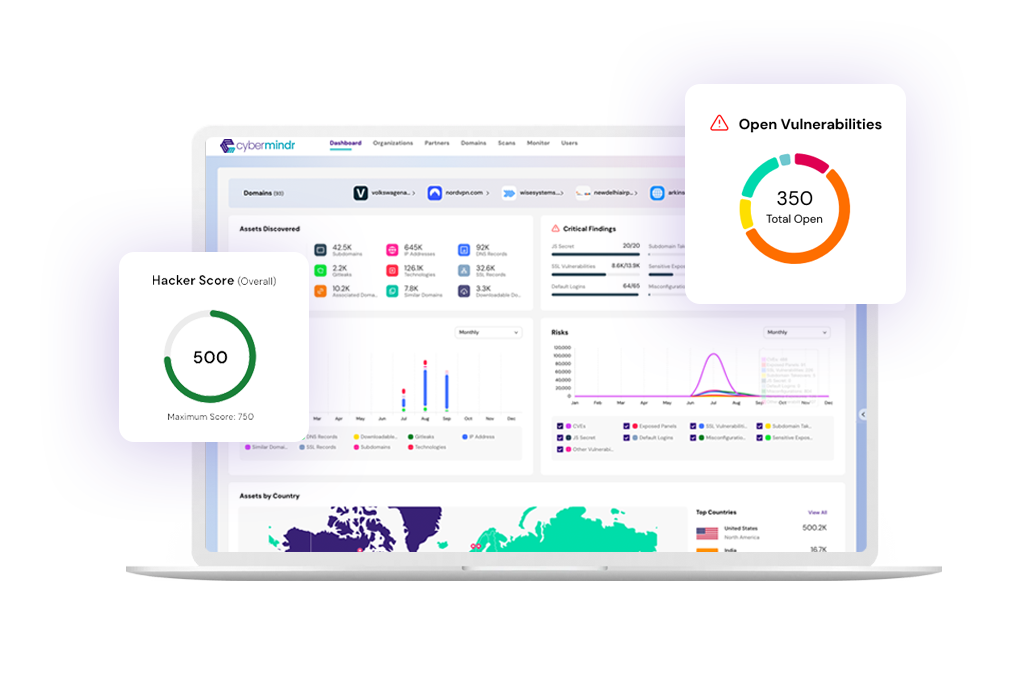
Navigate Cyber Threats
This approach to identify “real vulnerabilities” and “confirmed attack paths” helps you to prioritize remediation efforts with limited resources before they are exploited.
The Cybermindr Platform takes a different approach and shows only the validated-vulnerabilities and confirmed attack-paths. The platform performs 15,000+ live checks on the discovered assets and is continuously updated with new live check playbooks based on the ongoing monitoring of 300+ hacker forums to gather intelligence on attackers’ Tactics, Techniques and Procedures (TTPs).
This approach to identify “real vulnerabilities” and “confirmed attack paths” helps you to prioritize remediation efforts with limited resources before they are exploited.
cybermindr platform
Explore your technology stack comprehensively, from deployed technologies, Domains, Associated Domains, Subdomains, IP Address, DNS Records, SSL Certificates, Technology Stack etc.

Uncover publicly accessible code with potential security risks, exposed API keys, Gitleaks, Javascript keys, backup and hidden files etc.
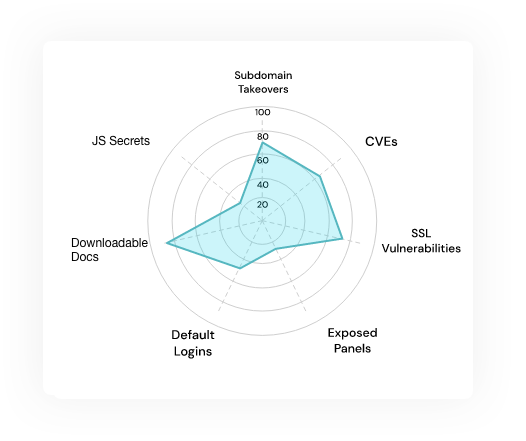
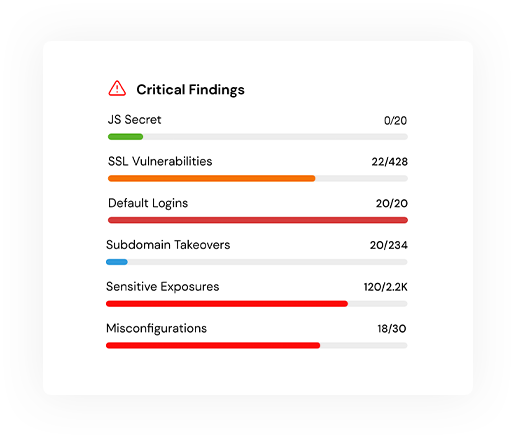
Proactively identify misconfigurations, SSL issues, exposed panels, CVEs (vendor-specific vulnerabilities) and exploitability concerns, Default Credentials, etc.
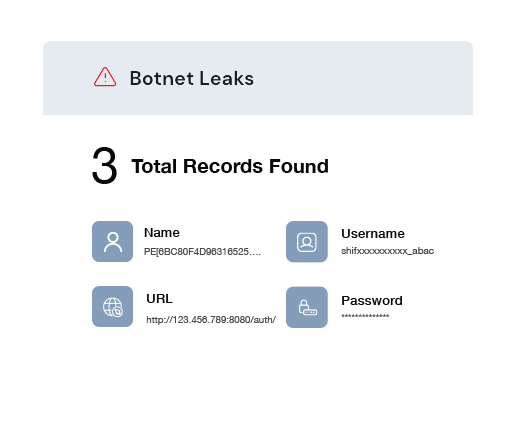
Detect botnet leaks and track leaked credentials currently in circulation on hacker markets & dark web to safeguard your sensitive information.
usecases
Take a proactive approach to protecting your data and systems before a cyberattack leads to data breaches, financial losses or reputational damage.
Pinpoint weaknesses in your security posture, prioritize remediation efforts, and fortify your defenses.
Read more

Gain insights into the cybersecurity posture of your portfolio companies
Read more

Meet regulatory requirements, streamline audits and avoid costly fines.
Read more

Safeguard your assets by minimizing potential risks from third party technologies that your organization uses.
Read more

Conduct in-depth evaluations of potential acquisitions or partnerships.
Read more

Scan through layers of the internet to uncover both known and unknown and unmonitored digital assets.
Read more
Resources
